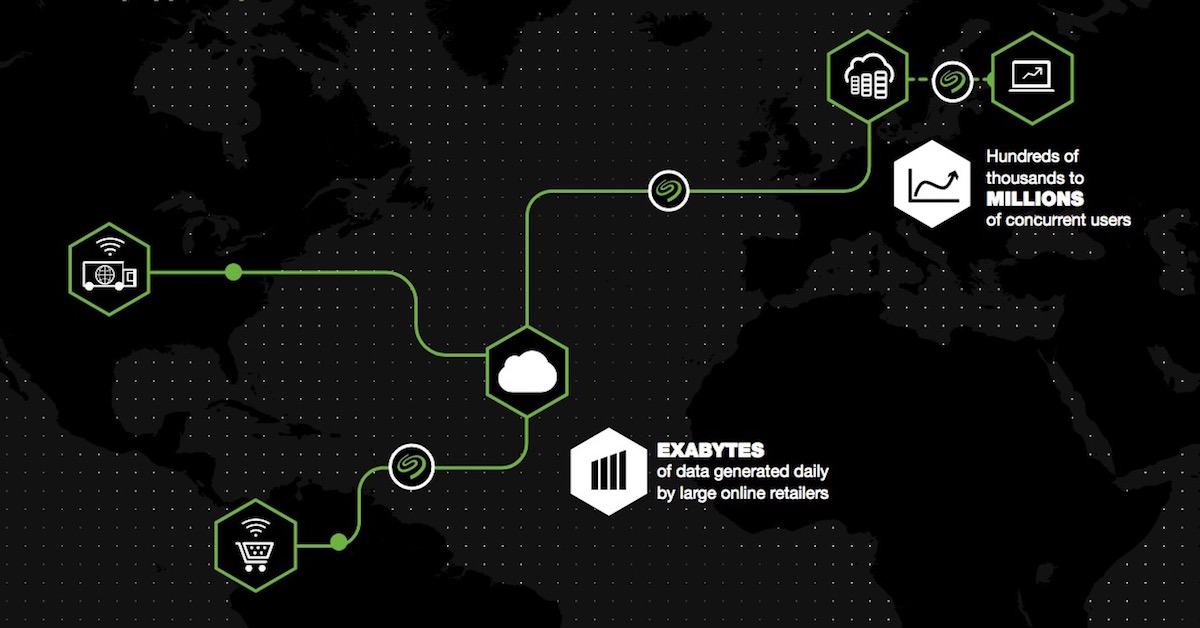
Trends such as the consumerization of IT have shifted the focus of business technology investments to improving end-user experiences. Success stories surrounding bring-your-own-device suggest that this holds some key advantages for companies, as users able to leverage their own devices for work may become more productive. A similar movement has been seen in the cloud storage industry, with many users pushing for organizational acceptance of third-party services.
Data Center Knowledge contributor Bill Kleyman recently noted that traditional motivations for cloud adoption revolve around IT efficiency. However, he suggested that more focus will soon be given to how the technology impacts user experiences and how to best leverage it to improve employee satisfaction and increase productivity.
"As more organizations begin to leverage cloud technologies, they will turn their focus to optimizing the end-user experience.," Kleyman wrote. "Furthermore, they are going to try their best to optimally deliver more workloads with better resource utilization, both at the data center and at the end-user level."
One of the key advantages for employees is the added flexibility afforded by cloud infrastructure. As Kleyman noted, a remote workforce can now access the same resources and digital assets as those working in the office. This allows for more flexible schedules and improvements in work-life balance. Additionally, the cloud supplements the consumerization trend by making enterprise applications accessible from anywhere.
Shifting toward the end user
The challenge for cloud service providers moving forward will be meeting the demands of end-user-centric IT strategies while still accommodating enterprise security concerns. Kleyman predicted that companies will start looking for "complete user abstraction" or services that allow employees to carry settings and data across many devices. Enterprise cloud storage solutions are also likely to become more prominent, as offerings such as Dropbox have not met the stringent security requirements of many businesses.
There is still some enterprise resistance to BYOD, but the trend's momentum is likely to continue over the next several years. Gartner analysts recently predicted that 50 percent of organizations will even require employees to use their own devices by 2017.
"BYOD strategies are the most radical change to the economics and the culture of client computing in business in decades," said Gartner vice president and analyst David Willis. "The benefits of BYOD include creating new mobile workforce opportunities, increasing employee satisfaction, and reducing or avoiding costs."
Although hardware procurement costs are often lower in BYOD environments, the trend creates a number of organizational challenges. For instance, business decision makers must grapple with how to enable secure access to corporate resources and must deal with more diverse IT environments. As Gartner noted, security has always been a top concern. However, companies are showing increased confidence in their ability to leverage BYOD without putting corporate data at risk.
Many of the other issues BYOD presents can be addressed by cloud storage. By enabling file-sharing and collaboration solutions with enterprise-grade security, providers can take advantage of this trend's momentum and further empower end users. According to Willis, it will be essential to identify clear user privileges and for IT departments to increase employee awareness surrounding common threats.
Cloud providers may face greater demand for transparency in their service-level agreements as well as expectations that their offerings can be utilized on a wide range of platforms. Another important factor to consider in the coming years is that many mobile initiatives are launched without a clear vision of business goals or potential risks. This means that technology providers may need to also act as consultants in identifying which cloud solutions are best suited for their customers' IT environments and which security features are necessary to protect sensitive data.