In my experience, over the last 10 years, as an IT engineer and architect I have answered my fair share of disaster recovery, network engineering, database administration and project management queries. Even in my role as an advisor on technical research projects, to my alma mater, Ryerson University I have addressed similar questions and concerns. But for each of these specific issues there is one underlying theme – data security.
Whether the setting is a Fortune 500 company or a university, data security within an organization should be evaluated through three main criteria: Confidentiality, Integrity, and Availability.
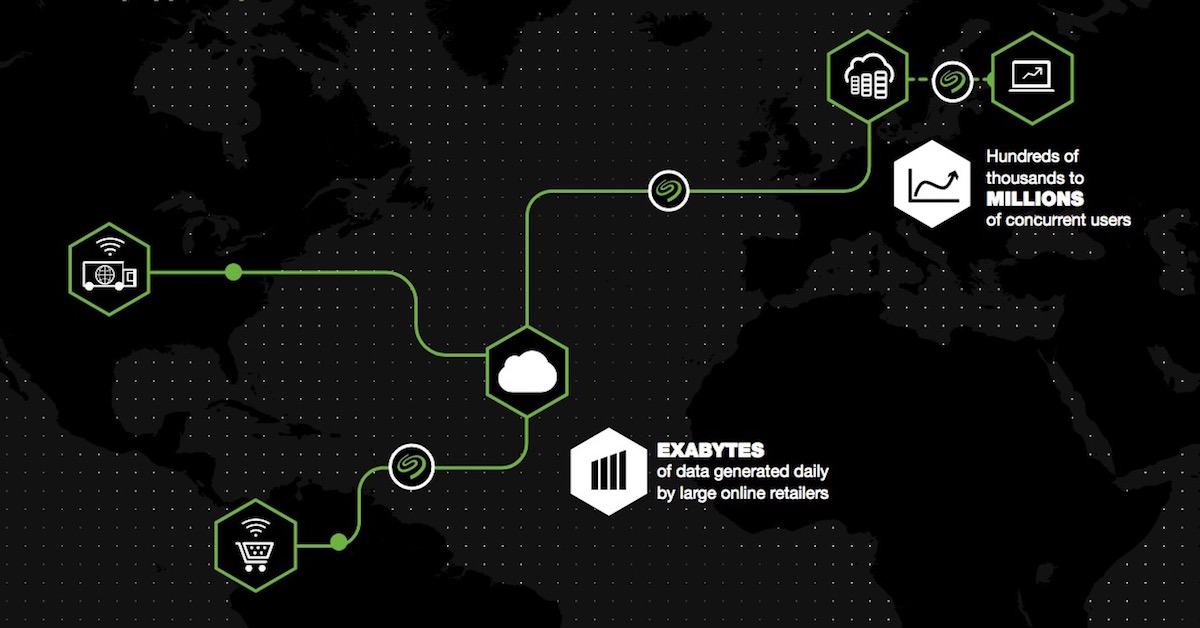
Inasmuch as cloud storage and file sharing platforms provide convenience they also come with potential risks of exposing vulnerabilities in data security. It is therefore crucial that users employing these tools also rely upon a security model with policies that protect both organization and employee data. A password policy is compulsory to this approach but is only the first step in establishing comprehensive data security.
- Confidentiality in data security is synonymous with encryption. But the notion of encrypted data does not guarantee confidentiality because, by definition and design, encryption implies decryption. In other words it becomes a matter of who will have the privilege in the act of decrypting. Will it be the intended user, or a hacker? The strength of encryption keys, where it is stored, how it is applied to the authentication process, and the authentication interface itself are all relevant factors, which can make or break data confidentiality.
- Integrity of data refers to the reliability considerations and raises a number of questions. How do you know the data you sent will end up in the cloud and in exactly the same consistency? Are there processes or technologies in place to ensure that, as time goes by, data in the cloud remains intact? If an error or some corruption occurs with the data, will there be automatic notification of the incident and is there a subsequent healing process? If not data integrity is compromised. Without these security measures in-place you may not know in-time and will be forced to recover lost data from a bad copy. For these reasons data integrity, which speaks to the importance to maintain consistency of original data, is an important security consideration.
- Data availability is the last piece to these security measures. Because cloud storage is often deployed in an extended topology – where local software is required to access the data – there is the chance of a “headless state” occurring. In simplest terms this is when the local software is not available and so too is the data stored in the cloud. For this reason, inherit to the availability of data is flexibility and simplicity. It should not require multiple stages of procedures for companies or employees to access data when they need it.
To learn more about Seagate’s secure approach to cloud and file sharing platforms visit our Cloud Systems and Solutions page on our website.