Cet article vous a-t-il été utile ?
Comment pourrions-nous l'améliorer ?
Using Account API
Account API allows you to access Lyve Cloud account information through an API endpoint. The account API can be generated only by the account administrators. You can perform all Lyve Cloud operations using the account API credentials.
What can I do with Account API?
Account API enables customers and sub-account administrators to leverage Lyve Cloud account's functionality programmatically.
You can perform the following actions using account API:
- Permissions: Create permissions, List permissions, Get permissions by ID, Delete permissions by ID, and Update permission
- Service Accounts: Create service account, List service account, Get service account data by ID, Update service account, Enable service account and Disable service account.
- Usage: Get current month storage usage and historical storage usage by month.
For more information, see Lyve Cloud Account API version 2.
The API uses the secure HTTP/1.1 over TLS 1.2 protocol and operates mainly with JSON-formatted messages. All API responses are assigned specific numeric codes that help you quickly identify if a request to an endpoint is successful or unsuccessful. For more information on error codes, see List of API error codes in the Account API version 2.
Generating Account API credentials
The credentials never expire when generating API credentials unless you configure an expiration duration. You can change the default setting by setting an expiry duration for all newly created API credentials; see Setting expiration duration. This limits the validity of the Account API credentials, which need to be changed again after the expiration. After the expiration date, the secret credentials cannot be used for authentication but will stay associated with the account until you delete or regenerate it.
- On the Header pane, select the username in the top right.
- Select Generate Account API Credentials.
- Copy or download the Access Key and Secret Key after you create the Account API credentials.
The status of credentials will show as one of the following. The status is based on the expiration duration.
- Expires in: XX days: You must generate the API credentials to use the API after expiration.
- Never Expires: The security credentials are not set, and these credentials will never expire.
- Expired: The credentials have expired, and you cannot access the account API.



After the credentials are generated, use these credentials to generate a time-bound token. This token is used to authenticate the Lyve Cloud Account API and is passed as a Bearer header value.
You must attempt to generate credentials the second time if Account API generation fails.
Regenerating Account API credentials
You can re-generate the credentials regardless of their expiration status. If you already have active credentials and still regenerate new credentials, the old credentials become inactive.
- On the Header pane, select the username in the top right.
- Select Generate Account API Credentials., and then select Regenerate.

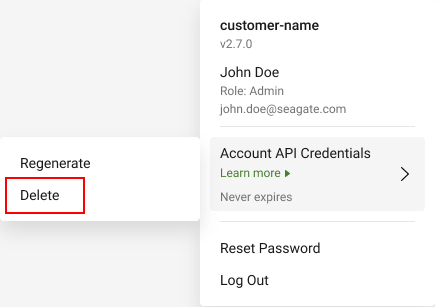
Deleting Account API credentials
Once you delete the credentials, you can again generate new credentials. However, any workload that uses these credentials will immediately lose access to the resources.
- On the Header pane, select the username in the top right.
- Select Generate Account API Credentials., and then select Delete.