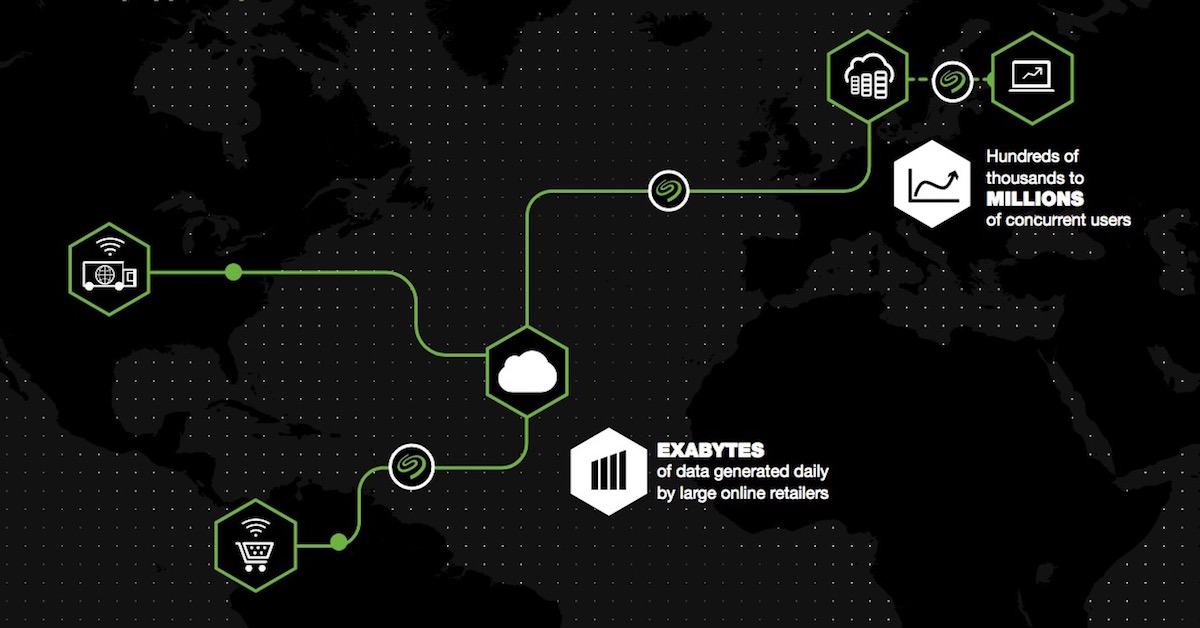
We’ve all heard the stories about data breaches: Target’s customer data base is compromised, the NSA spies on its own citizens, the Heartbleed bug leaves huge numbers of private keys and other internet information vulnerable.
Despite all this, the cloud remains not only a viable option for backup but one of the best and most secure.
Conversations about the cloud are intertwined with security. And while security concerns persist, more and more organizations are adopting hybrid cloud data protection solutions after evaluating all the options.
How can you bring the many benefits of a hybrid cloud solution to your organization with the minimum risk and maximum security? Find a hybrid cloud solution vendor that can provide on and off-site products and services that are connected and adhere to the highest security standards.
Here’s a list of what you need from your hybrid cloud data protection vendor:
- End-to-end encryption: There is no compromise here, this is the key to security. Your data must be encrypted through every step of the backup process—from the source server through data transmission and while in storage. Start at the source–before your data leaves the server, protect it with military grade 256-bit AES (Advanced Encryption Standard encryption). As your data travels over the Internet to the vault, insist that it’s protected by 256-bit AES encryption. Note that some large security vendors may claim to provide end-to-end encryption but don’t provide encryption on the client side.
- FIPS-approved AES encryption: You deserve the assurance of knowing encryption is certified by NIST (National Institute of Standards and Technology) as specified by FIPS (Federal Information Processing Standards) Publication 197. FIPS 197 designates AES as the standard for encrypting data used by federal departments and agencies. FIPS-approved encryption modules comply with that standard.
- Trust no one: Controlled data access means you alone own the encryption key, and your data center cannot access your systems. You want no back doors so you can be certain that no one else can access or decrypt your backup data.
- SSAE E16 compliant data centers: ensure that your is housed in a top-tier rated and ISO-certified or SSAE (Statement on Standards for Attestation Engagements No. 16) compliant environment. Systems-based SSAE 16 addresses service organizations and comprises guidelines and principles for “trusted” data security, confidentiality, integrity, availability, and privacy controls. At-rest encryption: your data must stay safely encrypted while in ISO-certified or SSAE (Statement on Standards for Attestation Engagements) 16-compliant data centers.
- Operational Controls/Operational Security: You must be able to easily track, backup and restore using detailed logs that create paper audit trails. You also need procedural, electronic, mechanical, and physical controls protecting the physical security of the data centers where your information is stored:
- Key-card and/or biometric access
- 24/7 surveillance cameras
- Background checks on all employees
- Data center access limited to authorized employees only
- Agent-initiated Backups: ensure all operations are authorized and authenticated
- Deduplication: ensures you back up only new or changed blocks, this ensures you expose much less data during the actual backup.
- Authentication and Authorization: you need to be in control from the moment you initiate the backup through communications and management. Both authorization and authentication are required to begin every backup and restore session so you know each one is completely cleared and approved. You need a solution will identify and validate the system,
 the account, and the username and network—and alleviate your concerns about unauthorized access.
the account, and the username and network—and alleviate your concerns about unauthorized access. - A Solution that Encrypts Interactions: with the management portal so you can configure your backup jobs and policies without compromising the security of your systems.
Is a hybrid cloud data protection more secure when you utilize a single vendor? Absolutely, but only if the data protection company has implemented the best practices above.
Curious to learn more? Would you like to get the facts behind some of the myths that persist about the risks of the cloud? If so click here to replay a corresponding and highly acclaimed webcast, which includes a lively presentation and Q&A session on how you can protect your organization.